Olli Isohanni
Phishing campaigns often use the same formula. An email that contains a link or an attachment is sent to the recipient with the purpose of retrieving data by directing the user to some fake web page on the internet, or by executing a malicious code from an attachment. This text presents the HTML tactic that is used for phishing. The text also presents a few methods which are used to discover and prevent scam emails. The tactic itself isn’t new, but the case studied in this text is a recent one. In this phishing tactic, an HTML attachment is sent to the target. If the target opens the attachment, it executes the malicious code and a phishing website runs locally in the target’s web browser.
Analyzing and understanding how different kinds of malicious links and malware works is interesting and useful for defensive purposes, but it is important to analyze them in a safe and isolated environment. Centria SecuLab has a malware lab environment where malicious programs and links can be tested safely.
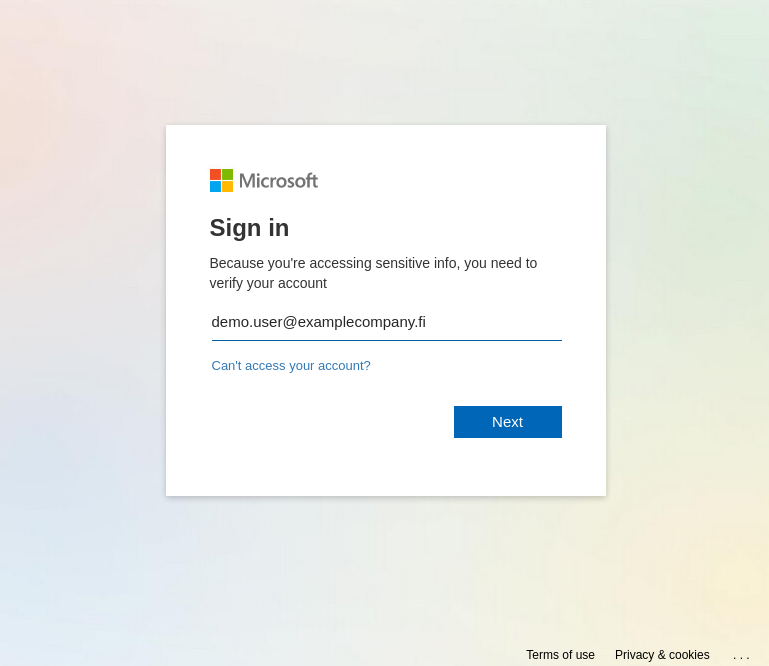
The investigated email was targeted to a specific individual as a notice of payment that was made recently. The only way to check this so called “payment” was to download the included attachment named “Remittance-copy” and to open it. This attachment opened a somewhat authentic looking Microsoft login page that had the targets email address already filled (see Picture 1 and Picture 2). This kind of targeted phishing is known as a spear phishing. For obvious reasons the original recipient address is changed.
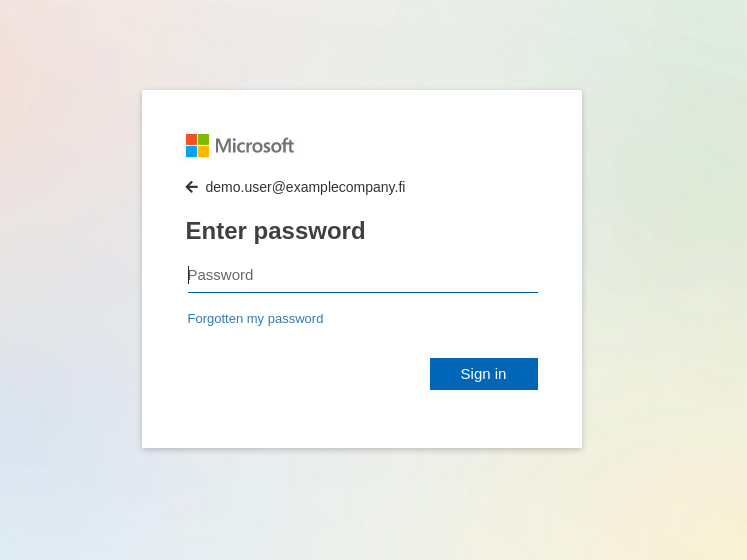
The password is always rejected at the first attempt as incorrect and only the second password is accepted (see Picture 3). Some users believe that phishing websites will always accept any password. Therefore, they assume that you can spot a phishing website by entering a wrong password as they believe that a phishing website will accept any password, while the legitimate site will reject it as incorrect (Hornetsecurity Security Lab 2020).
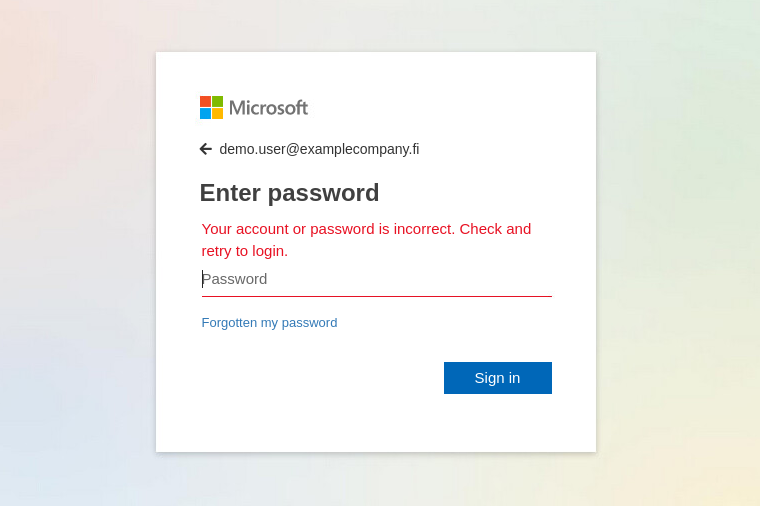
Every time the password is typed the second time the web page produces an output that is shown in picture 4. The message is clearly meant to deceive the user. Fortunately, in this case there was also a clear typing error in the message that raised suspicions about the authenticity.
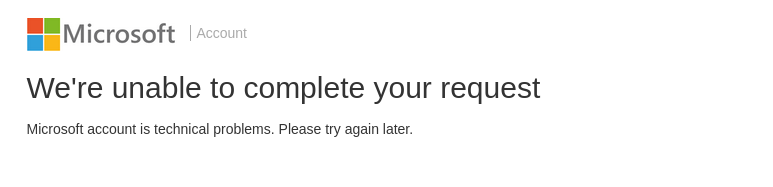
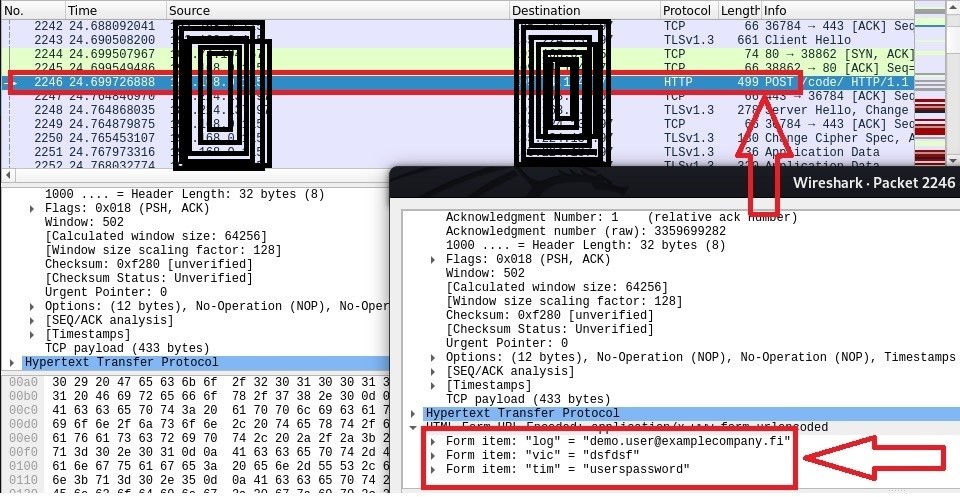
You can see from a Wireshark capture what happens when the password is provided the second time and login is attempted (see Picture 5). The capture shows that a POST request is made that includes the provided credentials. The red arrow in the bottom right corner of picture 5 points to the given credentials in the POST request.
This is quite a clever technique, because no online phishing site is needed. This method only needs a server that receives HTTP POST requests, so the server is less likely to be taken down. The webpage itself runs locally in the user’s browser, so in most cases warning messages about the page are not shown to the user.
The IP-address of the server receiving the POST requests was also visited (see Picture 6). The default page shows the hosting provider where the server is run, because no real website exists. However, cases exist where vulnerable websites are used for these purposes.

The phishing site code that runs in the user’s web browser is obfuscated, but there are several tools which can be used for cleaning and analyzing the code to better understand how it works. “Detonating” these malicious links and scripts in a safe and isolated environment gives information about their functionalities.
It is always important to check, who has sent the email you receive. In this case it was an unknown person from the email service hotmail.com. Look-alike domains are also used. In these cases, the email address is very close to the original.
About the project:
Cynic – Entrepreneurship & Security is a cross border project financed by Interreg Nord, Lapin liitto and Region Norrbotten. The project has been implemented together with Centria University of Applied Sciences and Luleå University of Technology. The main idea is to identify challenges for digital business sevelopment; test, experience and learn about data security, and exploration of emergent technologies. Project website
Reference:
Hornetsecurity Security Lab 2020. HTML Phising Asking for the Password Twice. Hornetsecurity Ltd, London. Published 7.4.2020. Verkkouutinen saatavissa: https://www.hornetsecurity.com/en/security-informationen-en/html-phishing-asking-for-the-password-twice/ . Referenced 29.4.2020.
Olli Isohanni
R&D Developer
Centria University of Applied Sciences
email firstname.lastname@centria.fi


